Sharing Your Internet Connection
So far, we have explored building a basic hardware network in your home, and we have explored the options you have in getting Internet service to your home. In this chapter, we will bring these together, along with our knowledge of IP networking to put all of the computers in your home onto the Internet.
TODO: LinkSys
More Computers - The Easy Way
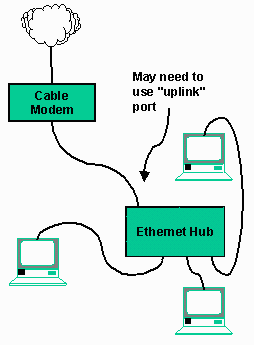 If your network connection is via DSL or a Cable modem, you may have a very simple option available to you. Some services will allow you to purchase additional IP addresses to your home for a small increase in your overall monthly fee (about $5.00 per address). They may be able to give you up to some small number (say 4) total addresses for your home.
If your network connection is via DSL or a Cable modem, you may have a very simple option available to you. Some services will allow you to purchase additional IP addresses to your home for a small increase in your overall monthly fee (about $5.00 per address). They may be able to give you up to some small number (say 4) total addresses for your home.
All that is necessary is to extend your network with an Ethernet hub. If the Ethernet port on your cable modem or DSL modem connects directly to your computer, you may have to connect it to the uplink port of the Ethernet hub. Once the other computers are connected and configured to set their IP addresses dynamically, they will be given IP addresses by the ISP over the DSL or cable modem.
Some of the DSL or cable modems that you may use will already have the hub functionality built into them so you can connect the additional computers right to the unit.
If your Internet service does not provide additional addresses, or if you want more addresses than they can supply, or you simply do not want to pay for the additional addresses, there are still several options which allow you to share a single IP address among multiple computers.
Special Address Ranges
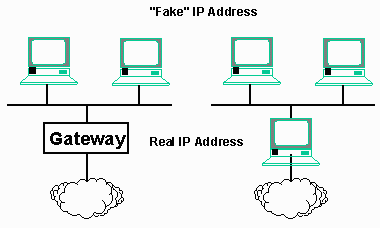 Given that we will only get one IP address from our Internet Service Provider, we will have to assign IP addresses to the other computers in the network. We will add special hardware and/or software to make these computers "seem" to be directly connected, their addresses are not truly global IP addresses.
Given that we will only get one IP address from our Internet Service Provider, we will have to assign IP addresses to the other computers in the network. We will add special hardware and/or software to make these computers "seem" to be directly connected, their addresses are not truly global IP addresses.
These addresses only need to be consistent your local area network so you could use any range of addresses for your LAN. However, at some point, there is a very small possibility that an IP address that you might pick might conflict with a real IP address. At that point, computers on your LAN would believe the address to be locally connected and never be able to see that server. While this might only happen once in several hundred million connections to the Internet, it is still not a good thing.
Fortunately, the designers of the IP protocol and the Internet anticipated this problem and reserved several special address ranges for this purpose. These ranges are called non-routable addresses. This means that they have absolutely no meaning within the Internet. If a packet with one of these addresses somehow makes it through a gateway and into the Internet, it will immediately be dropped. This allows these address ranges to be used for many different homes or even large corporations over and over for internal purposes. Each organization needs some sort of translating gateway to connect to the Internet, but then all of the computers appear to be on the Internet. This ability to add translating gateways allows far more computers to be using the Internet than the number of unique IP addresses.
The following are the non-routable address ranges:
10.*.*.*
172.16.*.* through 172.31.*.*
192.168.0.* through 192.168.255.*
You will notice that addresses of the form 192.168.1.* are used quite a bit in the examples throughout this book. These addresses are a very commonly used in home networks. When you receive vendor documentation for a home gateway, they will often simply tell you to use addresses in the 192.168.0.* range without even explaining why.
The 10.*.*.* address space is so large that an entire corporation could use the addresses internally for about 16 million computers and allow them all to access the Internet with a single (very large) address translating gateway.
Sharing One Address with Network Address Translation
The technology used to map many internal addresses through a single Internet address is called Network Address Translation (NAT). NAT is not an exact science and different implementations of NAT work better and worse for some of the different network applications. Luckily most of the typical applications we use such as web browsing, E-Mail, and file transfer work pretty well over NAT. These applications all use "connection oriented" protocols where they open a connection, transfer some data, and then close a connection.
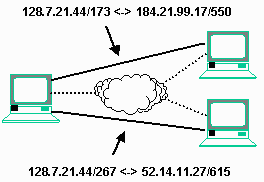 To gain an understanding of how NAT works, we first must delve a little more deeply into the TCP/IP protocol. While we think of connections as being between two computers, each with an IP address, in actuality there can be many connections between pairs of computers. Each connection is identified by the IP Address, port number, and connection number. The port number is a way that different applications communicate with the proper peer application on a remote system. For example web traffic moves over port 80 while E-mail is moved across port 25. For this NAT discussion, we will ignore the port number and concentrate on the IP address and the connection number.
To gain an understanding of how NAT works, we first must delve a little more deeply into the TCP/IP protocol. While we think of connections as being between two computers, each with an IP address, in actuality there can be many connections between pairs of computers. Each connection is identified by the IP Address, port number, and connection number. The port number is a way that different applications communicate with the proper peer application on a remote system. For example web traffic moves over port 80 while E-mail is moved across port 25. For this NAT discussion, we will ignore the port number and concentrate on the IP address and the connection number.
In this example, we have three computers numbered 128.7.21.44, 184.21.99.17, and 52.14.11.27. These computers are all connected directly to the Internet. The physical connections are shown as dotted lines so we can focus on the logical connections between the computers. The computer numbered 128.7.21.44 has two connections. The first connection is from its connection number 173 to the 184.21.99.17 connection number 550. These connection numbers (and port numbers) are used to "sort out" all of the packets and decide which application the data is destined for.
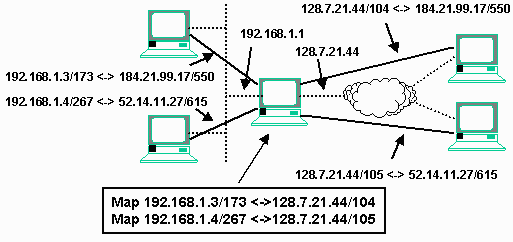 When NAT is used, we assign local addresses to our computers on our internal LAN. Those computers don't actually "know" that they are not connected to the Internet. The are configured with an IP address, subnet mask, and gateway address that makes sense on the local area network. When they make a connection to an address such as 184.21.99.17 that is not on their LAN, they simply forward the packet to the gateway address. Normally, the gateway simply copies the packet to the other connection and off it goes across the Internet. However when NAT is used, the packets which come into the gateway are routed to the NAT software.
When NAT is used, we assign local addresses to our computers on our internal LAN. Those computers don't actually "know" that they are not connected to the Internet. The are configured with an IP address, subnet mask, and gateway address that makes sense on the local area network. When they make a connection to an address such as 184.21.99.17 that is not on their LAN, they simply forward the packet to the gateway address. Normally, the gateway simply copies the packet to the other connection and off it goes across the Internet. However when NAT is used, the packets which come into the gateway are routed to the NAT software.
As connections are created, the NAT software maintains a table of network address mappings. It makes a connection to the destination computer using its own Internet address (128.7.21.44). This connection is assigned a connection number on the destination computer (550) and on the gateway system (104). The NAT software remembers all of the addresses associated with this particular connection. Once the pair of connections has been established, data begins to flow. The originating computer (192.168.1.3) sends data to the network gateway (192.188.1.1) destined for the ultimate destination (184.21.99.17). But before the data is forwarded to the Internet, the "return address" is changed from 192.68.1.3/173 to the values for the connection which the NAT gateway used to open the actual connection (128.7.21.44/104). Then the data is sent across the Internet.
The destination computer has absolutely no clue that this packet was "translated". The destination simply processes the data normally and returns data to the address specified in its incoming packet (128.7.21.44/104). When the gateway receives the data, it simply changes the destination address from its own address (127.7.21.44/104) to the computer on the local area network (192.168.1.3/550) and forwarded to the LAN.
While this all seems complicated, at the end of the day, it is all quite simple. For each connection, the NAT gateway maintains two connections. Packets are forwarded, except some of the addressing information is adjusted before it is forwarded. For outbound data, the source address/connection is changed before forwarding, and for returning data, the destination address/connection is changed before forwarding.
NAT works amazingly well. Over the years, more and more applications work well over NAT. Typically, when network access is packet oriented (as compared to connection oriented) some versions of NAT will fail. The most typical application which fails across a NAT gateway is network file sharing. So don't be surprised if your attempt to share network drives fails across a NAT gateway.
Sharing One Address With HTTP Proxy
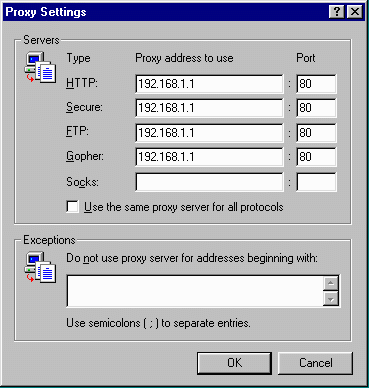 Another way to access the Internet when you are using non-routed network addresses is to use a World-Wide-Web proxy server. Using a proxy server only allows access to the world-wide web across the gateway. The proxy protocol is built-into most browsers as an option. There must be a computer with an Internet connection which is running the web proxy server software. Each client on the local network must be configured to use the proxy server and told which server (on the local network) to use for which protocols.
Another way to access the Internet when you are using non-routed network addresses is to use a World-Wide-Web proxy server. Using a proxy server only allows access to the world-wide web across the gateway. The proxy protocol is built-into most browsers as an option. There must be a computer with an Internet connection which is running the web proxy server software. Each client on the local network must be configured to use the proxy server and told which server (on the local network) to use for which protocols.
In more complex situations you may have different proxy servers for the different protocols. In a typical home situation there will be one gateway system which handles all of the proxy requests. It is also possible to do automatic proxy configuration. Automatic proxy configuration is generally much more common in the work environment than in the home environment.
The most important protocols in the configuration screen are the HTTP and FTP protocols. SOCKS is a protocol used to allow authenticated connections across the proxy. The most typical use of SOCKS is to allow a SOCKS-enabled FTP or telnet application to operate across the proxy. SOCKS is not very common in the home environment because it typically requires special versions of network applications.
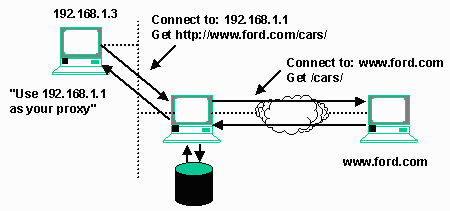 Once a client is configured to use a proxy, instead of directly connecting to a destination computer (www.ford.com), it sends a request to the "proxy" server which includes the entire URL which is being requested (http://www.ford.com/cars). When the proxy software sees this request, it makes the connection to www.ford.com, and retrieves the document using the standard Hypertext Transport Protocol (HTTP). When the data has been retrieved, the proxy system forwards a copy of the data to the originating workstation. This pattern is done repeatedly for every URL or file transfer performed by the browser.
Once a client is configured to use a proxy, instead of directly connecting to a destination computer (www.ford.com), it sends a request to the "proxy" server which includes the entire URL which is being requested (http://www.ford.com/cars). When the proxy software sees this request, it makes the connection to www.ford.com, and retrieves the document using the standard Hypertext Transport Protocol (HTTP). When the data has been retrieved, the proxy system forwards a copy of the data to the originating workstation. This pattern is done repeatedly for every URL or file transfer performed by the browser.
One advantage of the proxy protocol is that it is possible for the proxy server to store a copy of the web-pages and other files retrieved on a locally-attached hard disk. When a new request comes in for the same page, it can be satisfied simply by reading the data from the disk instead of re-retrieving it over the Internet. This caching web server approach has the advantage that it saves on precious network bandwidth and provides higher performance web surfing for the local clients.
Another advantage of a proxy server is that all accesses are typically logged including date, time, source computer and destination URL. Also proxy servers may allow the blocking of certain web addresses. In some ways, the proxy server acts as a simple firewall for outbound web access.
In some organizations, a proxy server is used even if the workstations have IP addresses which allow them to operate on the Internet. The performance improvement and connection savings are worth the use of the proxy server. One very popular proxy server package is called squid. In addition to operating as a basic proxy server as described above, squid also maintains a network of interconnected proxy servers. If your local squid server does not have the data you request, it requests the data from the next closest squid server. When used properly, the cooperating squid servers significantly reduce the amount of duplicate traffic which moves across an Intranet or the Internet.
Connection Sharing with NAT Software
Many users who already have a computer set up to access the Internet over a dial-up connection or another connection can extend that access to the rest of the computers connected to the home LAN simply by installing and configuring NAT gateway software on that computer. Three of the most popular software programs are
-
Sygate
-
Winroute
-
Windows-98 Second Edition - Connection Sharing
Installing and configuring this software is relatively straightforward (especially if you have been reading carefully up to now). We will take a look at a few of the configuration screens of the Sygate package performing network address translation between a phone modem connection and the home LAN.
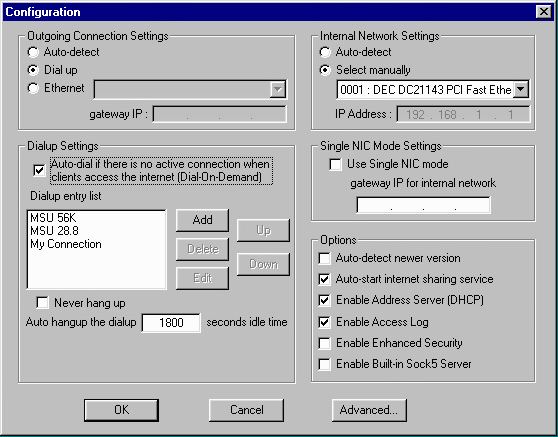
In the screen above, it is logically laid out with the left hand side describing the connection to the Internet (which happens to be dialup in this case). It can pick among several dial-up connections and switch from one to another when a busy signal is encountered. Sygate will automatically dial the modem connection when it receives network data destined for the Internet.
On the right hand side, it describes the connection to the Local Area Network. In the example, the address of the network card is 192.168.1.1 (a logical address for a "gateway").
In addition, there are check boxes to indicate whether or not we will be acting as a DHCP server on the local area network.
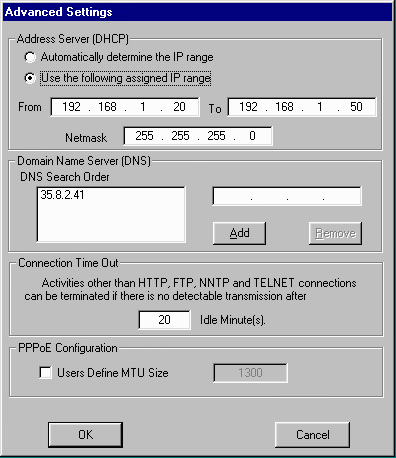 If we click on the Advanced button, we can configure the DHCP server and domain name server for the system. We can set the range of DHCP addresses which we will provide to clients. By limiting this range somewhat, we can also have static addresses on the LAN outside the range of 20-50. These static addresses can still use the gateway to connect to the Internet. We can also specify a Domain Name Server (always a numeric address). In the case of a dialup connection, this will be generally set as part of the PPP initialization. However if your Internet connection is a cable modem or other technology, you may have to hand-enter an address for the DNS server.
If we click on the Advanced button, we can configure the DHCP server and domain name server for the system. We can set the range of DHCP addresses which we will provide to clients. By limiting this range somewhat, we can also have static addresses on the LAN outside the range of 20-50. These static addresses can still use the gateway to connect to the Internet. We can also specify a Domain Name Server (always a numeric address). In the case of a dialup connection, this will be generally set as part of the PPP initialization. However if your Internet connection is a cable modem or other technology, you may have to hand-enter an address for the DNS server.
It is common for these gateways to act as a proxy domain name server. When Sygate replies to a DHCP request, Sygate indicates that its own gateway address (192.168.1.1) is what the client system should use for its DNS service. This way, Sygate software can reply to the DNS requests using a local value for a domain name lookup. This also gives Sygate some time to start to dial up the Internet before the client computer times out waiting for a network connection. By seeing the DNS packet, Sygate immediately knows that the next operation is very likely to be a connection to an Internet host. It also turns out that most network programs are willing to wait about 30 seconds for a response to a domain name query. However they typically only wait about 10 seconds before giving up on a connection to an IP address. By delaying the response to the DNS packet, Sygate can give itself about 40 seconds to dialup and initialize the network connection. All the client computer sees is a 30-40 second wait and then the page simply appears.
A nice advantage of a software solution is that you can see logs of activity. This can be helpful when diagnosing problems with your network or looking for activity patterns. Some gateways also have the ability to block or allow various network addresses on the Internet.
Even when your system is operating as a gateway, you can still use it as a workstation. The load on the system caused by performing the gateway functions is very small.
About the only disadvantages of using a software gateway are the fact that rebooting that computer disconnects all current network connections, and the system generally will be left on all the time. If the gateway system is not turned on, you must boot it up before you can use the Internet anywhere else in the house.
Connection Sharing with a Specialized Hardware Gateway
If you want a "more professional" gateway, you may want to opt for a hardware gateway. These products are also excellent, easy to use and easy to install/configure. Because they are hardware solutions, there is no need to install and/or maintain the software. The units are small, and once configured store their configuration in EEROM so if there is a power outage, they simply come back up in a few seconds or so. Some common hardware gateways include:
- Apple Airport
- 3Com OfficeConnect ISDN Modem
- Linksys Cable/Modem/DSL Router
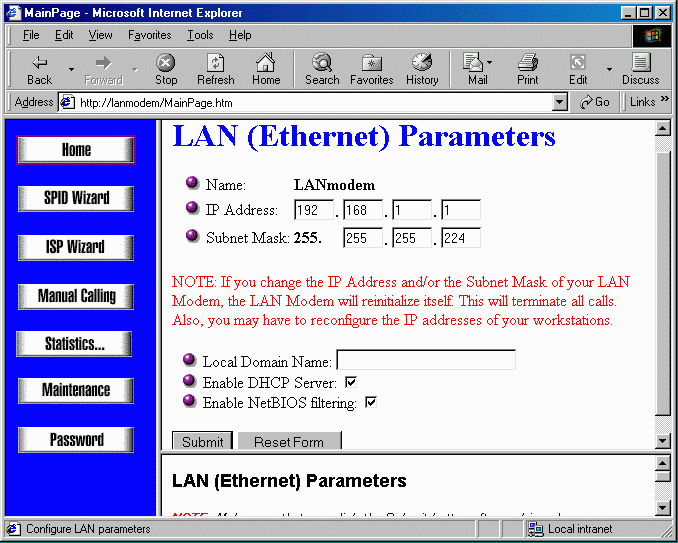
Many of these units are configured using a web browser. The 3Com OfficeConnect LanModem (3C892) is a unit which connects to an ISDN line, performs routing, network address translation, DHCP service for the LAN, has a built-in 4-port Ethernet hub and provides two POTS connections for a FAX or old-style telephone.
Knowing what you know from this book, its configuration is quite simple. You simply indicate its LAN address and subnet mask. Using the checkbox provided, you can cause the system to serve out DHCP address for network attached computers.
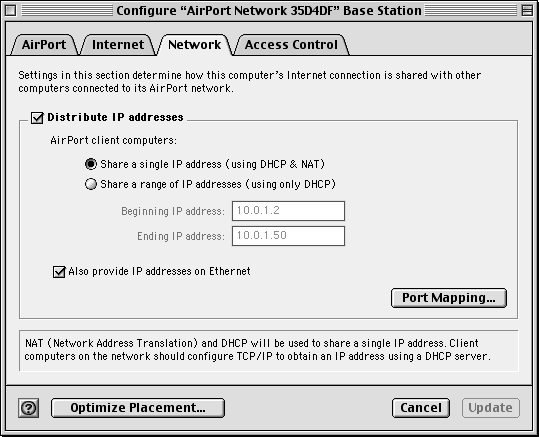
The Apple Airport unit is a very flexible and inexpensive home network gateway. It performs the same functions as the 3Com Office Connect except that it utilizes a standard analog modem. In addition to acting as a router, the Airport also has a wireless network card built-in and can act as the gateway between your wireless network, Ethernet network and the modem connected to the Internet.
To configure the Airport, you must use software which is provided for Macintosh computers. Even though the Airport must be configured using a Macintosh, its routing and wireless gateway are completely standard so they both can be used by Macintosh and PC computers.
The following screen configures the basic LAN parameters. In this example, we configure it to use DHCP and NAT. The Airport can be configured to serve DHCP addresses on the wireless network, both the LAN and the wireless network, or not serve DHCP at all.
TODO: LinkSys
Conclusion
While this chapter (like most) may have given you more detail about how shared Internet connections operate, unltimately configuring Internet sharing relatively straightforward. You can easily choose between a hardware or software solution. The configuration is surprisingly similar between the hardware and software solutions - this is because they ultimately are solving the same problem.
Software solutions generally have more flexibility and more logging options but are less convenient as they place one of your computers into a "server" role for the rest of the home. Hardware solutions are more expensive, but are generally more reliable.
 To gain an understanding of how NAT works, we first must delve a little more deeply into the TCP/IP protocol. While we think of connections as being between two computers, each with an IP address, in actuality there can be many connections between pairs of computers. Each connection is identified by the IP Address, port number, and connection number. The port number is a way that different applications communicate with the proper peer application on a remote system. For example web traffic moves over port 80 while E-mail is moved across port 25. For this NAT discussion, we will ignore the port number and concentrate on the IP address and the connection number.
To gain an understanding of how NAT works, we first must delve a little more deeply into the TCP/IP protocol. While we think of connections as being between two computers, each with an IP address, in actuality there can be many connections between pairs of computers. Each connection is identified by the IP Address, port number, and connection number. The port number is a way that different applications communicate with the proper peer application on a remote system. For example web traffic moves over port 80 while E-mail is moved across port 25. For this NAT discussion, we will ignore the port number and concentrate on the IP address and the connection number.
 If your network connection is via DSL or a Cable modem, you may have a very simple option available to you. Some services will allow you to purchase additional IP addresses to your home for a small increase in your overall monthly fee (about $5.00 per address). They may be able to give you up to some small number (say 4) total addresses for your home.
If your network connection is via DSL or a Cable modem, you may have a very simple option available to you. Some services will allow you to purchase additional IP addresses to your home for a small increase in your overall monthly fee (about $5.00 per address). They may be able to give you up to some small number (say 4) total addresses for your home.
 Given that we will only get one IP address from our Internet Service Provider, we will have to assign IP addresses to the other computers in the network. We will add special hardware and/or software to make these computers "seem" to be directly connected, their addresses are not truly global IP addresses.
Given that we will only get one IP address from our Internet Service Provider, we will have to assign IP addresses to the other computers in the network. We will add special hardware and/or software to make these computers "seem" to be directly connected, their addresses are not truly global IP addresses.
 When NAT is used, we assign local addresses to our computers on our internal LAN. Those computers don't actually "know" that they are not connected to the Internet. The are configured with an IP address, subnet mask, and gateway address that makes sense on the local area network. When they make a connection to an address such as 184.21.99.17 that is not on their LAN, they simply forward the packet to the gateway address. Normally, the gateway simply copies the packet to the other connection and off it goes across the Internet. However when NAT is used, the packets which come into the gateway are routed to the NAT software.
When NAT is used, we assign local addresses to our computers on our internal LAN. Those computers don't actually "know" that they are not connected to the Internet. The are configured with an IP address, subnet mask, and gateway address that makes sense on the local area network. When they make a connection to an address such as 184.21.99.17 that is not on their LAN, they simply forward the packet to the gateway address. Normally, the gateway simply copies the packet to the other connection and off it goes across the Internet. However when NAT is used, the packets which come into the gateway are routed to the NAT software.
 Another way to access the Internet when you are using non-routed network addresses is to use a World-Wide-Web proxy server. Using a proxy server only allows access to the world-wide web across the gateway. The proxy protocol is built-into most browsers as an option. There must be a computer with an Internet connection which is running the web proxy server software. Each client on the local network must be configured to use the proxy server and told which server (on the local network) to use for which protocols.
Another way to access the Internet when you are using non-routed network addresses is to use a World-Wide-Web proxy server. Using a proxy server only allows access to the world-wide web across the gateway. The proxy protocol is built-into most browsers as an option. There must be a computer with an Internet connection which is running the web proxy server software. Each client on the local network must be configured to use the proxy server and told which server (on the local network) to use for which protocols.
 Once a client is configured to use a proxy, instead of directly connecting to a destination computer (www.ford.com), it sends a request to the "proxy" server which includes the entire URL which is being requested (http://www.ford.com/cars). When the proxy software sees this request, it makes the connection to www.ford.com, and retrieves the document using the standard Hypertext Transport Protocol (HTTP). When the data has been retrieved, the proxy system forwards a copy of the data to the originating workstation. This pattern is done repeatedly for every URL or file transfer performed by the browser.
Once a client is configured to use a proxy, instead of directly connecting to a destination computer (www.ford.com), it sends a request to the "proxy" server which includes the entire URL which is being requested (http://www.ford.com/cars). When the proxy software sees this request, it makes the connection to www.ford.com, and retrieves the document using the standard Hypertext Transport Protocol (HTTP). When the data has been retrieved, the proxy system forwards a copy of the data to the originating workstation. This pattern is done repeatedly for every URL or file transfer performed by the browser.

 If we click on the Advanced button, we can configure the DHCP server and domain name server for the system. We can set the range of DHCP addresses which we will provide to clients. By limiting this range somewhat, we can also have static addresses on the LAN outside the range of 20-50. These static addresses can still use the gateway to connect to the Internet. We can also specify a Domain Name Server (always a numeric address). In the case of a dialup connection, this will be generally set as part of the PPP initialization. However if your Internet connection is a cable modem or other technology, you may have to hand-enter an address for the DNS server.
If we click on the Advanced button, we can configure the DHCP server and domain name server for the system. We can set the range of DHCP addresses which we will provide to clients. By limiting this range somewhat, we can also have static addresses on the LAN outside the range of 20-50. These static addresses can still use the gateway to connect to the Internet. We can also specify a Domain Name Server (always a numeric address). In the case of a dialup connection, this will be generally set as part of the PPP initialization. However if your Internet connection is a cable modem or other technology, you may have to hand-enter an address for the DNS server.

