Introduction
This article is the first of a two-part series that looks at the new
generation of WEP cracking tools for WiFi networks, which offer
dramatically faster speeds for penetration testers over the previous
generation of tools. In many cases, a WEP key can be determined in
seconds or minutes. Part one, below, compares the latest KoreK based
tools that perform passive statistical analysis and brute-force
cracking on a sample of collected WEP traffic. Next time, in part two,
we'll look at active attack vectors, including a method to dramatically
increase the rate of packet collection to make statistical attacks even
more potent.
Is WEP that bad?
Many security folks and even more wireless folks these days are saying
that WEP isn't all that bad. They say that if you use modern equipment that
filters weak Initial Vectors (IVs) and change your keys frequently (or at least once in a while),
nobody will ever crack your WEP. Sure, maybe some next-generation WEP attacks
will arise one day that will change everything, but WEP is okay today for all
but the most sensitive networks. Well, that next-generation is already here,
heralded by highly functional tools that make WEP look weaker than Barney Fife on
guard duty, sleeping on the job.
Let's take a look at some of the new tools that should be in every penetration
tester's bag of tricks, rather then delving into the details of why the various attacks work.
Time and time again, the industry has shown that it
will not reject broken security safeguards until attacks are actually
demonstrated in the real world. Here's how to quickly turn some heads.
The way things were
Since the summer of 2001, WEP cracking has been a trivial but time consuming
process. A few tools, AirSnort perhaps the most famous, that implement the
Fluhrer-Mantin-Shamir (FMS) attack were released to the security community -- who until then were aware
of the problems with WEP but did not have practical penetration testing tools.
Although simple to use, these tools require a very large number of packets to
be gathered before being able to crack a WEP key. The AirSnort web site
estimates the total number of packets at five to ten million, but the number
actually required may be higher than you think.
The first caveat to this old approach is that only encrypted packets count. As wireless access
points transmit unencrypted beacons several times per second, it is easy to be
fooled into believing that you have a larger number of useful packets than you
really do. If you use Kismet for network discovery and sniffing, it breaks
down the packet count for you, displaying the number of "Crypted" packets
separately from the total number, as shown below:
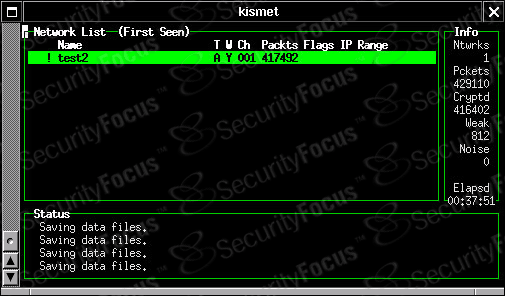 Figure 1. Kismet in action.
Figure 1. Kismet in action.
The second thing working against your packet collection efforts is that only
certain "interesting" or "weak" IVs are vulnerable to attack. Kismet also
tells you how many of these have been gathered, although it may not use the
same counting method as the various cracking tools. To make matters more
difficult, wireless manufacturers responded to the FMS attack by filtering out
the majority of weak IVs that their access points and wireless cards transmit.
Unless your target network is using old equipment, chances are you'll have to
collect no less than ten million encrypted packets to crack a WEP key using
these older tools.
In early 2002, h1kari released a tool called dwepcrack (part of the
bsd-airtools package) that improved upon the existing implementations of the
FMS attack. Although dwepcrack did a good job of advancing the practical
implementation of statistical WEP cryptanalysis, its improvements were only
incremental.
Tools that changed everything
On August 8th, 2004, a hacker named KoreK posted new WEP statistical
cryptanalysis attack code (soon to become a tool called chopper) to the
NetStumbler forums. While chopper is functional, it is not currently
maintained, and the attacks have since seen better implementations in aircrack
and WepLab. However, the KoreK attacks change everything. No longer are millions of
packets required to crack a WEP key; no longer does the number of obviously
"weak" or "interesting" IVs matter. With the new attacks, the critical
ingredient is the total number of unique IVs captured, and a key can often be
cracked with hundreds of thousands of packets, rather than millions.
Aircrack
The first tool in our new WEP cracking toolbox is aircrack by Christophe
Devine. Implementing KoreK's attacks as well as improved FMS, aircrack
provides the fastest and most effective statistical attacks available. To
give aircrack a try, simply collect as many packets as possible from a WEP
encrypted wireless network, save them as a pcap file, and then start aircrack
from the command line.
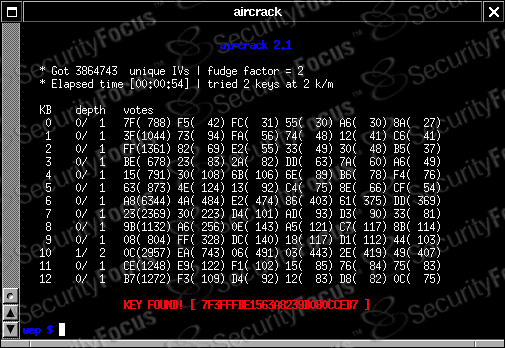 Figure 2. aircrack succeeds.
Figure 2. aircrack succeeds.
How many packets does it take?
The number of packets required for success with aircrack varies greatly. As a
rule of thumb, shoot for a minimum of 200,000 for a 64 bit key and 500,000 for
a 128 bit key, and remember to count only encrypted packets with unique IVs,
not total packets. aircrack comes with a handy packet capture tool called
airodump that keeps a running tally of unique IVs (the counting method is
imperfect but soon to be fixed) and is capable of handling very large capture
files. Personally, I find it easier to use Kismet most of the time and simply
estimate the number of unique IVs based on the number of "Crypted" packets
reported by Kismet. The number of encrypted packets with unique IVs is
typically more than 95% of the total number of encrypted packets.
How long does it take?
I often find that aircrack determines a WEP key within a few seconds, but the
execution time is highly variable. Shorter execution times require more
unique IVs, more luck, and the lowest successful "fudge factor," a setting
that tells aircrack how wildly it should guess when trying new keys. The
higher the fudge factor, the more keys aircrack will try, increasing both the
potential time of execution and the likelihood that the attack will succeed.
The fudge factor has a default value of two but may be set to any positive
integer. The default setting may be a good place to start, but trying several
different settings is frequently fruitful if the initial attack does not
succeed. I have encountered some data sets that could be cracked with a fudge
factor of one, several that could only be cracked with three, four, or higher,
and one data set that could only be cracked with a fudge factor of 31 or
higher.
The higher the fudge factor, the more branches aircrack will take. This
generally results in a longer execution time unless a successful crack
happens early in the process. The following graph shows the time of execution
as reported by aircrack (not counting file loading and parsing) for a
particular data set with various fudge factors. Blue dots represent the time
required for a successful crack and red dots represent the time spent in a
failed attempt.
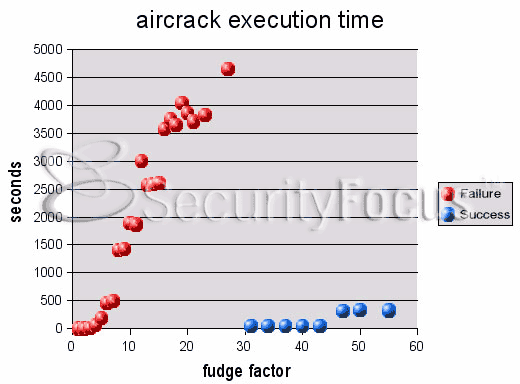 Figure 3. aircrack execution times.
Figure 3. aircrack execution times.
If the default fudge factor (two) fails, I usually double it for each
subsequent attack on the same data set. By terminating any attack that takes
longer than five or ten minutes, I have had good luck finding a successful fudge
factor fairly quickly.
One of the nice features of aircrack is that it works for both 64 bit and 128
bit WEP keys by default. If you know the key length of the target network,
giving the length to aircrack as a command line option can speed up the
process.
WepLab
Although not quite as successful in my tests, Jose Ignacio Sanchez's WepLab
provides an alternative implementation of the KoreK attacks that can be nearly
as effective as aircrack, with a little experimentation. Similar to aircrack's fudge
factor, WepLab provides a probability adjustment with its --perc command line
option. The default --perc setting of 50% is fairly aggressive and results in
relatively few branches, while higher settings increase the number of branches
taken. In addition to excellent statistical attacks, WepLab provides brute
force and dictionary cracking attacks that can be very effective. This
combination of techniques makes WepLab an essential tool.
Comparing the tools
WepLab and aircrack are certainly impressive, but are they the best tools in
the box? To find out, I performed a series of tests comparing the ability of
several statistical WEP cracking tools. To set up the test, I configured a
wireless access point with a random 128 bit WEP key, generated a great deal of
traffic, and collected about 25 million encrypted packets. I then carved up
the capture into shuffled subsets of various lengths and tried to crack each
subset with each tool, measuring the number of seconds for every successful
crack (including file load times). Trials that lasted more than ten hours
were terminated. The results surprised me quite a bit.
| Data Packets |
Weak IVs |
Unique IVs |
128 bit Cracking Time in Seconds |
| aircrack |
aircrack (4) |
AirSnort |
WepLab |
WepLab (95) |
WEPCrack |
dwepcrack |
| 23457438 |
8560 |
16775533 |
Failed |
245 |
92 |
Failed |
244 |
Failed |
Error |
| 21016149 |
1807 |
16775167 |
Failed |
249 |
41 |
Failed |
247 |
Failed |
Failed |
| 19584364 |
9340 |
16275925 |
Failed |
230 |
114 |
Failed |
229 |
Failed |
Failed |
| 15690079 |
8694 |
12860342 |
Failed |
184 |
90 |
Failed |
179 |
Failed |
Error |
| 15628308 |
5505 |
12361369 |
Failed |
176 |
70 |
Failed |
174 |
Failed |
Failed |
| 11743639 |
8473 |
11743639 |
Failed |
154 |
69 |
Failed |
153 |
Failed |
Error |
| 11739339 |
3037 |
11693841 |
Failed |
150 |
Failed |
Failed |
151 |
Failed |
Failed |
| 7829104 |
1001 |
5031233 |
Failed |
74 |
Failed |
Failed |
77 |
Failed |
Error |
| 7799213 |
5225 |
7779299 |
Failed |
87 |
37 |
Failed |
101 |
Failed |
Failed |
| 4175159 |
1554 |
4069824 |
52 |
51 |
Failed |
Failed |
54 |
Failed |
Failed |
| 3914568 |
767 |
3914568 |
Failed |
Failed |
Failed |
Failed |
Failed |
Failed |
Error |
| 3914553 |
3958 |
3914553 |
48 |
49 |
Failed |
Failed |
56 |
Failed |
Error |
| 3884657 |
1490 |
3864743 |
48 |
46 |
Failed |
Failed |
52 |
Failed |
Failed |
| 978652 |
986 |
978652 |
Failed |
Failed |
Failed |
Failed |
11 |
Failed |
Error |
| 978633 |
371 |
978633 |
Failed |
12 |
Failed |
Failed |
13 |
Failed |
Error |
| 977219 |
264 |
974902 |
Failed |
9 |
Failed |
Failed |
13 |
Failed |
Failed |
| 684992 |
143 |
684992 |
8 |
8 |
Failed |
Failed |
11 |
Failed |
Error |
| 683605 |
238 |
681288 |
Failed |
18 |
Failed |
Failed |
13 |
Failed |
Failed |
| 587184 |
117 |
587184 |
Failed |
27 |
Failed |
Failed |
Long |
Failed |
Error |
| 489293 |
103 |
489293 |
8 |
7 |
Failed |
5 |
5 |
Failed |
Error |
| 489286 |
115 |
489286 |
15 |
16116 |
Failed |
Failed |
Long |
Failed |
Error |
| 391465 |
78 |
391465 |
5 |
13 |
Failed |
Failed |
Long |
Failed |
Error |
| 391433 |
78 |
391433 |
Failed |
6 |
Failed |
Failed |
6 |
Failed |
Error |
| 293596 |
65 |
293596 |
Failed |
5 |
Failed |
Failed |
Long |
Failed |
Error |
| 293579 |
65 |
293579 |
Failed |
Failed |
Failed |
Failed |
Failed |
Failed |
Error |
Table 1. 128 bit WEP Cracking Times (in seconds).
Although aircrack was successful with the greatest number of data sets, it did
not perform as well as I expected with the default fudge factor. In fact,
beyond about four million packets, its success rate with default options
noticeably declined with the addition of more packets. This problem was
easily remedied, however, by increasing the fudge factor. A fudge factor of
four was successful in nearly every case. In the few cases in which a fudge
factor of four did not work, I was able to find a successful setting in the
five to twenty range.
WepLab's nearly complete failure with default options was surprising, but a
little experimentation resulted in a --perc setting of 95% that rivaled
even aircrack's best results. For some data sets, WepLab was more successful than
aircrack; for others, aircrack was the winner. Overall, both tools yielded
outstanding results with minor tweaking, though aircrack edged out WepLab in
the smaller data sets.
AirSnort's success rate matched my expectations quite closely, cracking nearly
every key with ten million or more packets but failing most of the time when using a
smaller data set. AirSnort's speed beat out aircrack and WepLab in every
case. Of course, an extra minute or two is rarely a concern, so the superior
cracking ability of the KoreK attacks with far less required input puts WepLab and aircrack
well above AirSnort in my book.
The most unexpected results were the total failures of WEPCrack and dwepcrack
with all data sets. WEPCrack came up with as many as eleven out of thirteen
correct bytes but always included incorrect bytes in its final result.
Lacking a process to verify the correctness of a key, WEPCrack produced a
false positive result every time. dwepcrack failed in every case, complaining
of either "insufficient ivs," the inexplicable error, "unable to find a valid
data packet in logfile," or, for my largest data set, "File too large." As
the tests were performed under Linux, perhaps dwepcrack would be more
successful in its native BSD environment.
Don't ignore the obvious
WepLab and aircrack make statistical attacks alarmingly easy, but many keys
can be cracked without going to such lengths. The simple fact is that most
people don't choose strong encryption keys, in part because vendors make it so
easy to use weak ones. Because of this weakness, a great number of WEP
encrypted networks are vulnerable to dictionary or brute force attacks that
only require the capture of a single encrypted data packet to attempt.
The simplest brute force attack involves trying every possible binary key, a
process that is completely impractical for 128 bit keys but may be worth
trying for 64 bit keys if you have a few supercomputers lying around. WepLab
and dwepcrack provide the ability; you provide the CPU cycles.
WepLab and WepAttack both provide two dictionary attack methods, one based on
the more common MD5 hashing technique that many access points use to turn a
passphrase into a binary WEP key, and the other using null terminated raw ASCII
WEP keys, employed by a few devices. Knowledge of the target network hardware
may help to determine which method would be preferred for a particular
environment.
Because both of the above tools can use any dictionary in a text file or standard input,
powerful password cracking utilities such as John the Ripper may be used to
generate the word list. Combined with John's ability to apply rules (various
capitalizations, appending numbers, etc.) to a basic dictionary, these tools
result in a successful crack surprisingly often. Although both performed
dictionary attacks successfully in my tests, WepLab executed faster while
WepAttack provided the convenience of multiple simultaneous attack modes.
If a dictionary attack fails, an optimized brute force attack based on the
vendor's passphrase method may be fruitful. For devices that use null
terminated ASCII keys, WepLab offers a brute force attack that only tries
ASCII bytes, resulting in a somewhat smaller (though still generally too
large) key space. For the more common MD5 hashed passphrases, dwepcrack can
execute an optimized brute force attack for 64 bit keys. This method, devised
and first implemented by Tim Newsham, dramatically reduces the potential key
space from 2^40 to 2^21 possible keys, resulting in an extremely fast attack.
The complete toolbox
Featuring the most effective statistical attacks available, aircrack may be
the single most important tool in the box. WepLab is also essential,
providing several techniques including an excellent alternative implementation
of the KoreK attacks. AirSnort may be worth trying if you have a lot of
packets to work with, but its position as statistical attack leader has been
usurped. WepAttack is a nice addition for dictionary attacks, and dwepcrack
provides the most fruitful brute force technique. The only other essential
ingredient is a method to collect packets; while most of these tools include
packet gathering as a built-in ability or ancillary program, I personally
prefer Kismet for this function. All of these tools are available in the
Auditor Security Collection live Linux CD-ROM.
Concluding part one
Looking at the outstanding success rate of aircrack and WepLab in the 500,000
to 1,000,000 packet range, it is clear that a new era is upon us. Vendors'
efforts to limit the transmission of weak IVs have been blown away, and the
time required to collect packets for a successful statistical attack has been
reduced twentyfold. If you thought WEP was okay, think again.
All of the tools discussed so far are completely passive, receiving data but
transmitting nothing. In part two, we will look at active WEP attacks,
including a method to dramatically increase the rate of packet collection,
making statistical attacks even more potent. Fasten your seat belts.
|

